Testing is a crucial part of the software development lifecycle. It helps ensure that applications function as intended and are free of vulnerabilities before deployment. With the rise of DevOps and continuous delivery, having fast and effective testing methods is more important than ever. Three commonly used approaches for testing code quality and security are static analysis, dynamic application security testing (DAST), and static application security testing (SAST). But what's the difference between these methods and when should each be used? This article provides a comparison of static analysis, DAST, and SAST to help inform testing strategy.
What is Static Analysis?
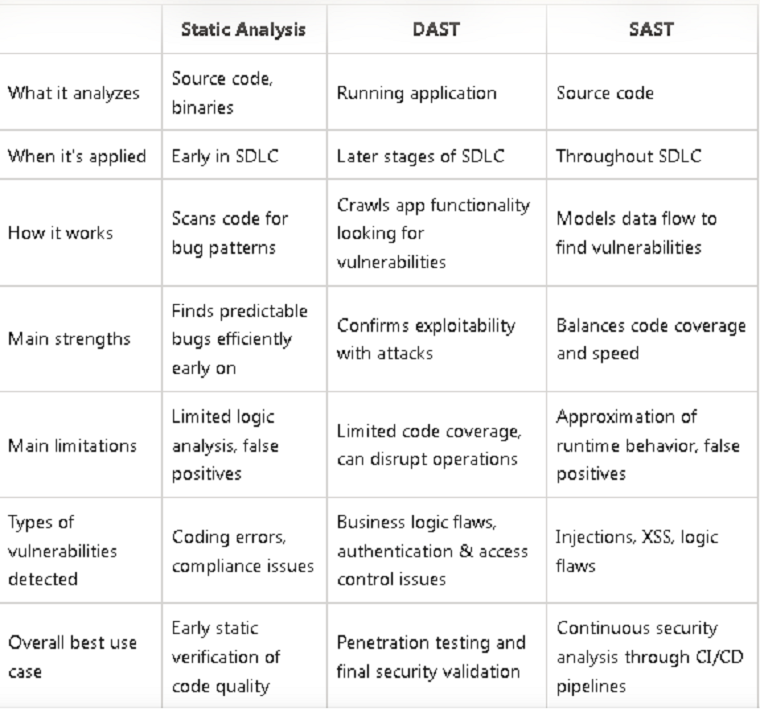
Static analysis examines application code without executing it. It analyzes source code, byte code, and binaries to detect bugs, security flaws, and quality issues. Static analysis tools scan code for patterns that are known to cause specific problems, such as buffer overflows, SQL injections, and cross-site scripting.
The key advantage of static analysis is it identifies vulnerabilities and quality issues early in the SDLC, before code is deployed. This allows developers to remediate problems efficiently at the coding stage, rather than having to deal with bugs later on. Static analysis can be performed iteratively as code is being written, giving rapid feedback to programmers. It scales well, enabling large codebases to be scanned quickly.
However, static analysis has some limitations. It may generate false positives - warnings about code that isn't actually problematic. Some tools have high false positive rates that can overwhelm developers with inaccurate alerts. Static analysis also cannot catch all types of bugs, especially logical flaws that require code execution to detect. And while it can find where vulnerabilities may exist, it does not confirm actual exploitability.
Overall, static analysis is best suited to finding coding bugs, compliance issues, and predictable security weaknesses in source code. It serves as an efficient early testing step to improve code quality before release.
The key advantage of static analysis is it identifies vulnerabilities and quality issues early in the SDLC, before code is deployed. This allows developers to remediate problems efficiently at the coding stage, rather than having to deal with bugs later on. Static analysis can be performed iteratively as code is being written, giving rapid feedback to programmers. It scales well, enabling large codebases to be scanned quickly.
However, static analysis has some limitations. It may generate false positives - warnings about code that isn't actually problematic. Some tools have high false positive rates that can overwhelm developers with inaccurate alerts. Static analysis also cannot catch all types of bugs, especially logical flaws that require code execution to detect. And while it can find where vulnerabilities may exist, it does not confirm actual exploitability.
Overall, static analysis is best suited to finding coding bugs, compliance issues, and predictable security weaknesses in source code. It serves as an efficient early testing step to improve code quality before release.
What is Dynamic Application Security Testing?
DAST analyzes applications while they are running, attempting to find security issues in the dynamic behavior and responses. DAST tools crawl through an application to discover all possible execution paths. As it explores the app's functionality, it monitors network requests and analyzes the responses to identify potential vulnerabilities, such as injection flaws, path traversal issues, and improper access control enforcement.
Unlike static analysis, DAST validates actual exploitability by attacking the application as an authenticated user would. This enables it to find security flaws that static analysis would not, like business logic errors. DAST also has low false positive rates compared to static tools.
On the downside, DAST only sees behavior that its test cases trigger, so code coverage is limited. It also requires the application to be up and running, which isn't feasible early in development. And DAST can disrupt operations by overwhelming apps with attacks, requiring runtime monitoring to avoid availability issues.
Overall, DAST is ideal for finding security bugs closer to production, complementing static analysis. It's well-suited for penetration testing and validating vulnerability remediation later in the SDLC.
Unlike static analysis, DAST validates actual exploitability by attacking the application as an authenticated user would. This enables it to find security flaws that static analysis would not, like business logic errors. DAST also has low false positive rates compared to static tools.
On the downside, DAST only sees behavior that its test cases trigger, so code coverage is limited. It also requires the application to be up and running, which isn't feasible early in development. And DAST can disrupt operations by overwhelming apps with attacks, requiring runtime monitoring to avoid availability issues.
Overall, DAST is ideal for finding security bugs closer to production, complementing static analysis. It's well-suited for penetration testing and validating vulnerability remediation later in the SDLC.
What is Static Application Security Testing?
SAST combines elements of static and dynamic analysis. Like static analysis, it analyzes source code without executing it. But SAST also analyzes data flow to model how input data propagates through code, enabling it to detect some logical vulnerabilities that require understanding execution paths.
SAST tools build a representation of the application's expected runtime behavior by modeling data flows from entry points like APIs. This enables SAST to find security flaws like SQL injections and cross-site scripting that depend on understanding how user input gets processed. SAST solutions can also incorporatesimulated execution engines to approximate real usage scenarios. This provides coverage of complex code paths that static analysis alone would miss.
A major advantage of SAST is it balances code security coverage with runtime overhead. SAST avoids the extensive computational resources required for exhaustive DAST scans by strategically modeling only parts of the code relevant for finding vulnerabilities. This makes SAST suitable for regular use within CI/CD pipelines, where speed and efficiency are critical.
However, like static analysis, SAST can have false positives due to not actually running code. Tuning is required to reduce misleading alerts. SAST also does not confirm real exploitability like DAST penetration testing. And its data flow analysis is an approximation of runtime behavior, meaning it does not have full code coverage.
In summary, SAST hits a middle ground between static and dynamic testing. It expands on static analysis to find more security issues with less overhead than full DAST scans.
Key Differences Between the Testing Approaches
SAST tools build a representation of the application's expected runtime behavior by modeling data flows from entry points like APIs. This enables SAST to find security flaws like SQL injections and cross-site scripting that depend on understanding how user input gets processed. SAST solutions can also incorporatesimulated execution engines to approximate real usage scenarios. This provides coverage of complex code paths that static analysis alone would miss.
A major advantage of SAST is it balances code security coverage with runtime overhead. SAST avoids the extensive computational resources required for exhaustive DAST scans by strategically modeling only parts of the code relevant for finding vulnerabilities. This makes SAST suitable for regular use within CI/CD pipelines, where speed and efficiency are critical.
However, like static analysis, SAST can have false positives due to not actually running code. Tuning is required to reduce misleading alerts. SAST also does not confirm real exploitability like DAST penetration testing. And its data flow analysis is an approximation of runtime behavior, meaning it does not have full code coverage.
In summary, SAST hits a middle ground between static and dynamic testing. It expands on static analysis to find more security issues with less overhead than full DAST scans.
Key Differences Between the Testing Approaches
When to Use Each Approach
Static analysis, DAST, and SAST each have their own strengths making them suitable for different stages of the development lifecycle:
Consider combining approaches for comprehensive testing. For example, use static analysis and SAST early on, followed by DAST later before release. A blended strategy catches different types of vulnerabilities throughout the SDLC.
Prioritize speed and efficiency early on, then shift focus to increased coverage later as code solidifies. Lightweight static and SAST scans give rapid feedback without slowing development. Heavier DAST scans provide deep validation before deployment.
- Use static analysis early on during coding to find and fix predictable bugs efficiently. Scan code iteratively as it is developed to improve quality.
- Use SAST throughout the SDLC to continuously analyze code and catch security flaws through CI/CD integration. Its speed and enhanced logic analysis make it ideal for dev and QA.
- Use DAST later in the cycle once apps are running to validate vulnerabilities and exploitability through penetration testing exercises.
Consider combining approaches for comprehensive testing. For example, use static analysis and SAST early on, followed by DAST later before release. A blended strategy catches different types of vulnerabilities throughout the SDLC.
Prioritize speed and efficiency early on, then shift focus to increased coverage later as code solidifies. Lightweight static and SAST scans give rapid feedback without slowing development. Heavier DAST scans provide deep validation before deployment.
Key Factors to Consider
Choosing the right testing approach involves weighing several key factors:
Companies must balance these factors based on their specific priorities, constraints, and objectives. For example, testing mission-critical software may require extensive coverage using both SAST and DAST despite greater effort. Testing simple web apps early on may need just lightweight static scanning.
- Stage of SDLC - When is testing needed? Early, middle, late?
- Frequency of testing - How often will testing be repeated? Fits in CI/CD?
- Coverage needs - How much of the codebase needs analysis?
- Vulnerability focus - Which flaw types are most concerning?
- App complexity - How complex is the application logic?
- App availability - Can runtime disruption be tolerated?
- Skill level - What tester expertise is available?
- Reporting needs - What kind of reporting is optimal?
- Tool costs - What is the testing budget?
Companies must balance these factors based on their specific priorities, constraints, and objectives. For example, testing mission-critical software may require extensive coverage using both SAST and DAST despite greater effort. Testing simple web apps early on may need just lightweight static scanning.
Best Practices for Implementation
To gain the most benefit from SAST, DAST, and static analysis, keep these best practices in mind:
Static analysis, SAST, and DAST all play important roles in securing applications. Static analysis provides early, low overhead bug detection. DAST validates exploitability through penetration-style testing. SAST strikes a balance, with enhanced logic analysis compared to static tools but lower runtime impact than DAST. Organizations should utilize a blend of these approaches tailored to their needs at each SDLC phase. By combining complementary testing methods, companies can build robust defenses ensuring their software is safe, secure, and resilient end-to-end.
- Combine approaches for layered testing - for example, SAST for continuous checks plus DAST for release validation.
- Integrate tools into the SDLC - embed automated SAST checks in the CI/CD pipeline.
- Leverage automation to enable frequent recurring testing.
- Define clear protocols for handling findings - quick fixes vs documented risk acceptance.
- Use risk-based prioritization to focus on critical vulnerabilities first.
- Tune tools to minimize false positives based on application specifics.
- Validate findings with QA testing and code reviews to avoid false alarms.
- Supplement with manual testing like penetration testing for increased coverage.
- Track metrics over time to demonstrate reduced risk exposure.
Static analysis, SAST, and DAST all play important roles in securing applications. Static analysis provides early, low overhead bug detection. DAST validates exploitability through penetration-style testing. SAST strikes a balance, with enhanced logic analysis compared to static tools but lower runtime impact than DAST. Organizations should utilize a blend of these approaches tailored to their needs at each SDLC phase. By combining complementary testing methods, companies can build robust defenses ensuring their software is safe, secure, and resilient end-to-end.

